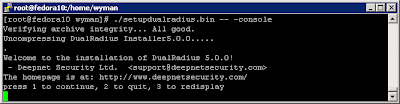
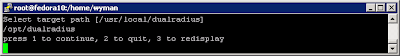
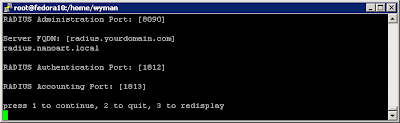
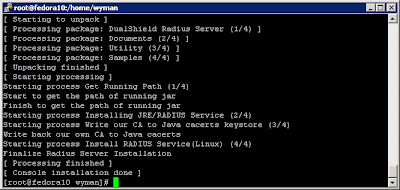
Deepnet Security hasn’t published the official document for how to use one of their products, MobileID Android version. Probably they assume you have an android phone and are familiar with the android OS, thus you can figure it out by yourself. Actually yes, as you will see, it is quite straightforward to use this app.
Download
The app can be downloaded with your phone’s browser at this link. Surely you can use other ways to install this app to your mobile phone.
Once installed, it looks like,
“Not token yet”, you can’t do anything! Don’t panic. If you think about it from a common sense perspective, you will try the “menu” button which each android phone is supposed to have.

Press it, you can see 4 menu items on the screen.
 Add Token
Add TokenTouch it to bring you another activity.
You can install a token with two different approaches. With the approach “By Download”, you need to input Service URL, Token Serial Number and Activation Code, get them from your deepnet service provider(DSP).
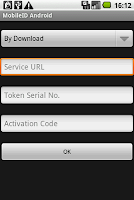
If your service provider doesn’t expose the service URL, then try the other approach “Install Locally”. This time you have to get Token Seed, Token Serial Number from your DSP, however you can name the “Token Name” of your own will.
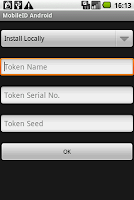
Once your click “OK” button, a new token will be added to your MobileID store, assume you have entered the correct data.
Now, touch the button “Generate OTP”, the OTP(s) will be generated and shown on the LCD area.

There are two buttons along with the bar which shows the current token’s name. The left one is an info button which shows the token information once you click it.
The right one is a sync button, it will synchronize the current token with Deepnet Authentication Server on the condition that this token is installed by download(it has a service URL).
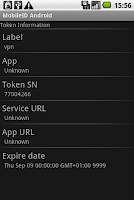
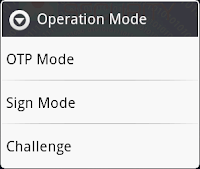
Do you notice a task bar at the bottom of the screen which shows the text “OTP Mode”? Hold it more than one second, a context menu will be shown, you can alter the mode among the three, OTP, Sign and Challenge.
Are you a VIP? Do you have many tokens to access different applications? If yes, you may ask such a question, how to easily switch the active token? Well, this app provides you a convenient feature: fling/swipe the area of current token, it will shift to the adjacent one based on your fling direction.
Management Token
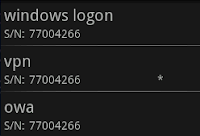
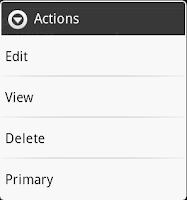
This activity lists all the tokens you have installed. Select a token by long click, it will pop up a context menu which allows you to delete a token, change the token name, view the token details and make the selected token as the primary(active) one(stated with the sign *).
Change PIN
Want more privacy? You can add a PIN to protect this app. There is no OK or Cancel button on this activity, you have to click the “Back” button to go back the main activity.

Now if you rerun the app(exit first), it presents the PIN page first, you have to enter the correct PIN so that you can access the normal OTP activity. Try with a wrong PIN, the app will show you a warning dialog saying how many times you can still try. If it reaches zero, sorry, the app will remove all tokens for security reason.

Exit
No statistic about how much battery power this app will consume during the idle. If you are concerned about this issue, press the menu item “Exit” for a fully quit to ease your mind.
It is said that all android phone with OS 1.5 or later can benefit from this app.